2. IPSEC - Internet Protocol Security |
IPSEC focuses on the security that can be provided by the IP-layer of the network. It does not concern itself with application level security such as PGP for instance.
We can divide the security requirements into two distinct parts:
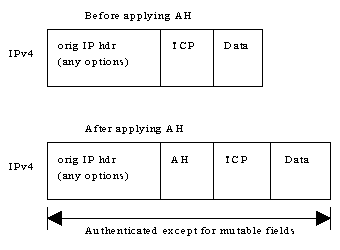
The Authentication Header (AH) is a mechanism for providing strong integrity and authentication for IP datagrams. It might also provide non-repudiation*, depending on which cryptographic algorithm is used and how keying is performed. The security is provided by adding authentication information (to the IP datagram) which is calculated using all of the fields in the IP datagram (including not only the IP header but also the other headers and the user data) which do not change in transit (for instance hop-count field in IPv6, and time-to-live field in IPv4, headers cannot be included as they are altered at each relay the datagram passes through).
To no surprise this system provides much more security than the current bare version of IPv4. Authentication might actually be sufficient for some users who do not require confidentiality. The argument for not using more security measure for some types of packets is the processing costs associated with computation of authentication data by the participating end systems. The authentication data is carried in its own payload, hence the systems which are not participating in the authentication may ignore it.
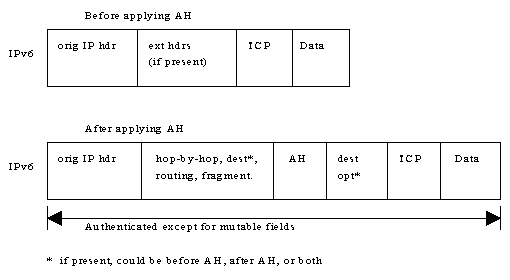
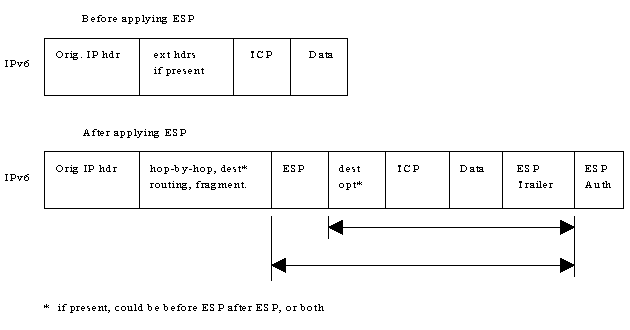
When used with IPv6, the AH is normally placed after the Fragmentation and End-to-End headers, but before the ESP and transport-layer headers (TCP or UDP for example). In IPv4, AH is placed immediately following the IPv4 header. Below are some examples of the IP header structures with and without the AH:
[Authentication Header example when used with IPv4]

[Authentication Header example when used with IPv6]
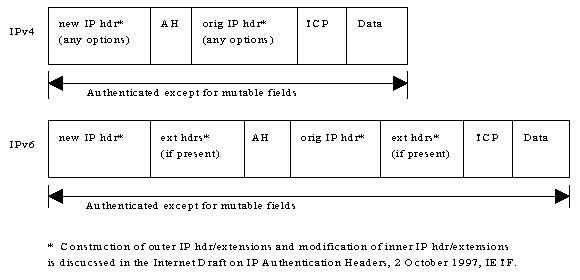
[Authentication Header tunnel mode positioning for typical IPv4 and
IPv6 packets]
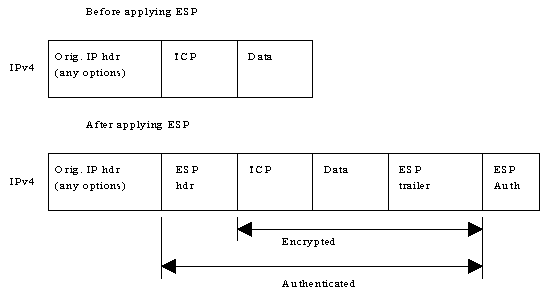
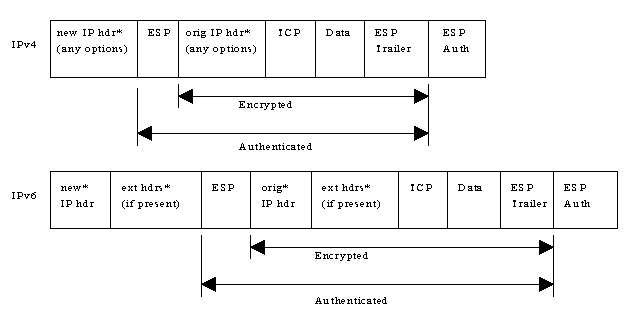
IPSEC provides confidentiality services through Encapsulating Security Payload (ESP). ESP can also provide data origin authentication, connectionless integrity, and anti-reply service (a form of partial sequence integrity). Confidentiality can be selected independent of all other services. There are two modes for providing confidentiality using ESP. One is transport mode, and the other is tunnel mode. Tunnel mode encapsulates an entire IP datagram within the ESP header. Transport mode, encapsulates the transport layer frame inside ESP (the term 'transport mode' should not be misconstrued as restricting its use to TCP and UDP).
When incorporating the ESP into the IP system (IPv4, IPv6, or Extension) the protocol header immediately preceding the ESP header will contain the value 50 in its Protocol (IPv4) or Next Header (IPv6) field.
Below are some examples how the typical IPv4 and IPv6 packets might look before and after applying ESP - transport mode:
And an example of tunnel mode:
A SA normally includes the following parameters:
[required]
All hosts claiming to provide IPSEC services must implement the AH with at least the MD5 algorithm using a 128-bit key as specified in the AH RFC. An implementation may support other authentication algorithms in addition to keyed MD5. All ESP implementations must support the use of the Data Encryption Standard (DES) in Cipher-Block Chaining (CBC) mode as detailed in the ESP specification. Other cryptographic algorithms and modes may also be implemented in addition to this mandatory algorithm and mode. MD5 and DES-CBC should be set as default algorithms.
Although this is arguably the most secure method to distribute keys, and the simplest one, it does not scale, and only works in very small, static systems. It can be used for LANs and some firewall systems, but is a short-term approach.
Work is currently under way to provide a secure, and efficient method for automatic key distribution. For more details please visit IETF web site.