3. TCM projects |
The first work concerning IPSEC in relation to the security project at the TCM laboratory was done by Timo Aalto who implemented IPSEC prototype using STREAMS under Solaris 2.5. This protocol was designed for IPv4 as an add-on to the existing implementations (this means that in this section reference to IP should be taken as reference to IPv4).
The purpose of the study was to build an IPSEC prototype and investigate its performance, portability, and possible extensions. The project has been based on the Requests For Comments (RFC), deployed by the IETF, as they were when it was started. Due to recent revisions, the original specifications have become somewhat outdated by now.
The use of STREAMS tries to assure that the code can be easily ported. However, objectively this may be hard to achieve, because it depends on existing TCP/IP implementations.
There are three ways to add the IPSEC to the IP protocol layer.
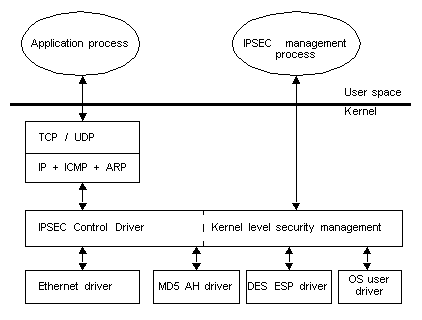
The diagram below presents the structure of this prototype. The architecture consists of a set of device drivers, a management module and interfaces between the subsystems:

The modularity of this design means that although only MD5 and DES-CBC are incorporated into this prototype, additional cryptographic transformation drivers can be added with ease (a cryptographic transformation driver is a module which encodes/decodes the data). The interface supports dynamic connections which saves resources.
The prototype implements manual key distribution which is OK for the purpose of testing this implementation. It is however possible to implement an automatic key distribution system and link it in if such need arises. Aalto stresses that it is crucial that IPSEC pays attention to the security of the keys on the host computer, otherwise the security gained through IPSEC may be lost.
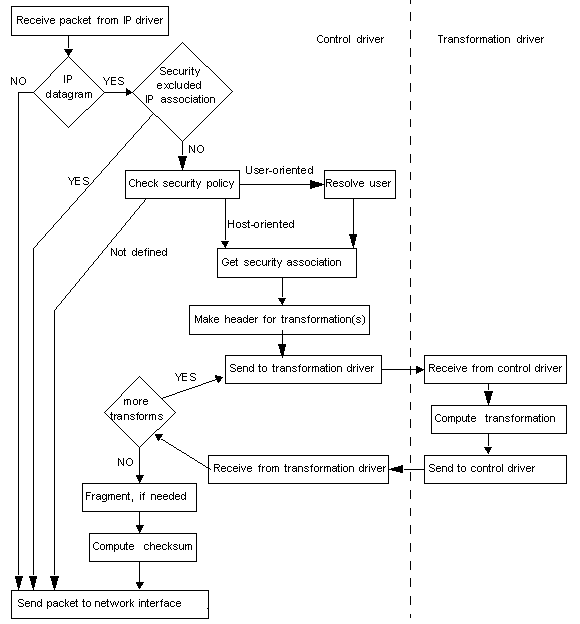
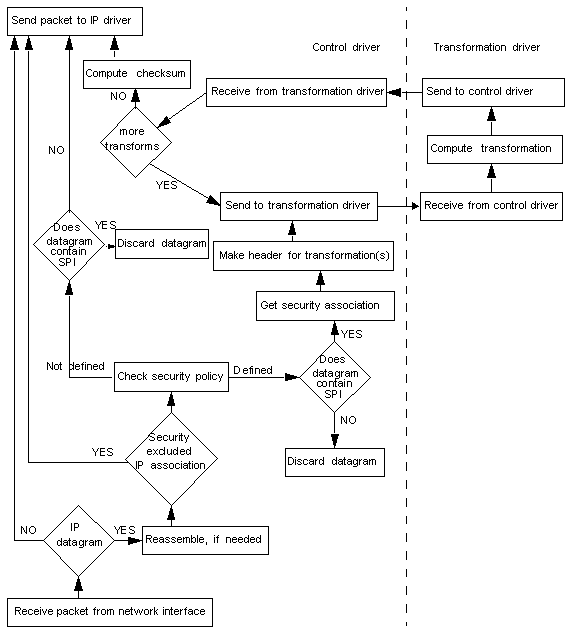
The two diagrams below present the IPSEC control logic for incoming and outgoing traffic:
[outgoing]
[incoming]
The performance of Aalto's prototype was evaluated by transferring a large file using rcp command from SUN SPARCStation 4 to SUN SPARCStation 1+ using 10MB/s Ethernet as transmission medium.
| Performance Measurement Values | |
| No IPSEC, no STREAMS | 315 kb/s |
| STREAMS without use of queues or context switches, no IPSEC | 237 kb/s |
| STREAMS with queues and context switches, no IPSEC | 56 kb/s |
| IPSEC without AH and ESP | 47 kb/s |
| IPSEC with AH | 26 kb/s |
| IPSEC with transport-mode ESP | 26 kb/s |
| IPSEC with tunnel-mode ESP | 26 kb/s |
| IPSEC ESP-part AH and tunnel-mode ESP | 19 kb/s |
| IPSEC with transport-mode ESP and AH | 20 kb/s |
| IPSEC with tunnel-mode ESP and AH | 18 kb/s |
The use of STREAMS mechanisms for handling messages incorporating only the put routine decreases performance by about 25%. The use of streams queues and service routine decreases the performance by about 80%. The performance drop is due to a number of extra context switches. Additional delays are caused by copying data. Hence most of the processing time in this prototype is spent on STREAMS processing.
Aalto suggests several solutions to the performance problem. Performance improvements must be examined through objectives for the implementation. If the current objectives: security, portability and modularity, stay, the performance can be improved by avoiding the use of queue and context switch whenever possible. All the IPSEC can be done within the same context unless congestion occurs on one of the drivers. This requires more sophisticated flow control handling compared to the current implementation. Performance can be improved to approximately 180-200 kb/s.
It may be beneficial performance-wise to eliminate the use of multiple STREAMS device drivers, and to do all the IPSEC processing within a single device driver. The modularity may be then preserved by designing functional interfaces within the driver.
By dropping portability, we can further increase performance. This requires implementing IPSEC as part of the IP layer. In the future it might also be possible to use dedicated hardware to compute the transformations. This has an advantage of offering extra security, but reduces the flexibility of the system.
If you would like to examine the project in more detail, please look up the thesis from the link page.