3. TCM projects |
Secure Open Transport (SecOT) prototype has been developed as a topic for Tik-76.115 Individual Project. The purpose was to implement an IPSEC prototype for the Macintosh Open Transport environment. The UNIX STREAMS implementation was used as design basis, and Timo Aalto coordinated the project.
Apple Open Transport is the modern networking and communications subsystem for Mac OS. Open Transport is based on industry standards and brings a new level of networking connectivity, control, and interoperability to MacOS systems, while preserving and enhancing the hallmark of the Macintosh and MacOS - build-in support for easy-to-use networking.
Open Transport development was started with assumptions that networking is inherently a multiplication, multi-protocol proposition; and that the customers should not have to start over to achieve networking interoperability. This defined five key design goals:
The C programming language was chosen for this implementation. Only the essential features were built into this prototype. The STREAMS mechanism used also handles the minimum amount of STREAMS messages; those needed for supporting IPSEC. Although logically IPSEC is implemented between TCP and IP, it proved easier to build it between IP and the hardware layer.
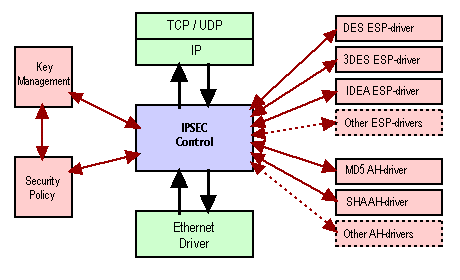
Internally IPSEC has been divided into modules, which use procedures to communicate with each other. The transformation modules (used for coding and decoding the packets) were implemented in such a way that addition of new transforms could be done with minimum effort.
[Structure of the implementation]

The design allows the program to be totally transparent to the user, and only a drop in transfer speed indicates its presence. Unlike the other designs though, this project did not opt for portability. The development lead to a very specific interface to communications hardware which makes porting difficult.
The working principle of the design is very simple. The control module for IPSEC resides between IP and the Ethernet driver. When IP sends a packet, the control module checks what kind of security policy there should be, applies the authentication or encryption (or both) to the packet, and forwards it to the Ethernet driver. Similarly upon receiving a packet from the Ethernet driver, it is validated by the transformation modules, and if it passes it, it is forwarded to the IP layer.
Upon any error (such as bad authentication/encryption and other) the packet is automatically discarded.
Despite a close working relationship with the Macintosh hardware, the code has been written in a way that would allow further development. The division of code into functional modules allows porting and modifications by upgrading or changing separate modules rather than a need to rewrite everything from scratch. It also allows a fairly easy way to add new modules, for instance better transforms.
A complete description of each of the modules of this prototype can be found from the project web page. The link page provides a link.
Because MacOS is currently a single-user operating system, there is no need for concern about security of keys on the host machine itself **.
At the time of the design, only manual key configuration was considered, hence this implementation (like the ones described earlier) needs manual key configuration, and is designed to work in small, static test environments. The testing was performed between two PowerMac 7200 machines.
The prototype was always tested as an entire package, not by single module performance.
Three different ways were used to test the working of the prototype:
Testing was done according to the following procedure:
Performance (speed-wise) of this prototype has not been tested.